In the contemporary digital landscape, the importance of safeguarding sensitive information cannot be overstated. As cyber threats continue to evolve, robust security measures are imperative to protect digital assets. At the forefront of these measures is the implementation of strong password encryption methods, which serve as a vital defense mechanism against unauthorized access. This article delves into the intricacies of such methods, offering insights into their necessity and effectiveness in fortifying digital security.
Read Now : Leading Schools For Software Development
Understanding Strong Password Encryption Methods
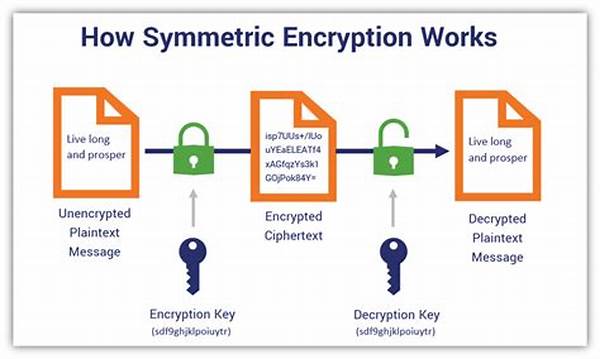
The essence of strong password encryption methods lies in their capacity to transform readable data into complex, encoded formats that are indecipherable without the correct decryption key. These methods are designed to ensure that even if passwords are intercepted, they remain unintelligible to potential intruders. The encryption process involves sophisticated algorithms that convert plain text into cipher text, protecting it from unauthorized access. One of the primary objectives of these methods is to enhance password security by preventing data breaches, which are often facilitated by weak or predictable passwords. By implementing strong password encryption methods, organizations and individuals can safeguard their sensitive information, thereby maintaining privacy and ensuring data integrity. In addition to thwarting cyber threats, these methods also play a crucial role in compliance with data protection regulations, which mandate the use of secure data handling practices.
The Significance of Strong Password Encryption Methods
1. Data Protection: Strong password encryption methods are pivotal in protecting sensitive data from unauthorized access, thereby reducing the risk of data breaches.
2. Regulatory Compliance: Many regulations require the use of strong password encryption methods to safeguard personal information, ensuring compliance with data protection standards.
3. Enhanced Security: By implementing strong password encryption methods, organizations can significantly enhance their security posture, making it difficult for attackers to exploit vulnerabilities.
4. Trust and Credibility: Utilizing strong password encryption methods bolsters consumer trust and assures stakeholders of an organization’s commitment to security.
5. Long-term Viability: Investing in robust encryption methods contributes to the long-term viability of digital infrastructures, allowing them to adapt to evolving security challenges.
Implementing Strong Password Encryption Methods
Strong password encryption methods are crucial for any organization seeking to protect its digital assets from unauthorized access. These methods utilize complex algorithms that are designed to scramble data in such a manner that only authorized parties can decipher it. The implementation of these methods requires a strategic approach that aligns with the organization’s overall security strategy. This involves not only the selection of appropriate encryption technologies but also the integration of these methods into existing security protocols.
Additionally, ongoing evaluation and updates of encryption strategies are essential to counteract emerging threats. The dynamic nature of cyber threats necessitates continuous adaptation and enhancement of encryption methods. Organizations must remain proactive, conducting regular audits to assess the effectiveness of their encryption solutions. By doing so, they can ensure that their strong password encryption methods remain formidable barriers against potential cyberattacks, thereby maintaining the confidentiality and integrity of sensitive data.
Evaluating Encryption Algorithms
Various algorithms are employed in strong password encryption methods, each with distinct characteristics:
1. AES (Advanced Encryption Standard): Highly efficient and widely used in various security protocols.
2. RSA (Rivest-Shamir-Adleman): Utilizes asymmetric encryption for secure data transmission.
3. Blowfish and Twofish: Known for speed and effectiveness in data encryption applications.
4. SHA (Secure Hash Algorithm): Often used for password hashing to ensure data integrity.
Read Now : Cross-industry Innovation Techniques
5. PBKDF2 (Password-Based Key Derivation Function 2): Increases the complexity of passwords through multiple hashing iterations.
6. Scrypt: Designed to resist hardware attacks, offering robust password protection.
7. Bcrypt: Adaptable to future computing power, making it a reliable choice for password security.
8. Elliptic Curve Cryptography (ECC): Provides high security with smaller keys.
9. Salts and Pepper: Enhances password security by adding random data to passwords before hashing.
10. Hybrid Encryption: Combines multiple encryption methods for added security.
11. Quantum-resistant Algorithms: Developed in anticipation of quantum computing capabilities.
12. HMAC (Hash-Based Message Authentication Code): Ensures data integrity and authenticity through a unique hashing process.
Future-Proofing Strong Password Encryption Methods
The importance of future-proofing strong password encryption methods cannot be understated. As technology advances, so do the tactics employed by cybercriminals. Therefore, organizations must remain vigilant and adaptive to these changes. Incorporating emerging technologies and proactive threat intelligence will be instrumental in staying ahead of potential vulnerabilities. This includes investing in training and development for IT personnel to ensure they are equipped with the latest knowledge and skills related to encryption technologies.
Furthermore, engaging in collaborative efforts with industry peers and cybersecurity experts can prove beneficial in sharing insights and strategies for improving security measures. By prioritizing the continuous evolution of encryption methods, organizations can ensure they remain resilient in an ever-changing threat landscape. Strong password encryption methods are, therefore, not merely a current necessity but a significant component in the ongoing endeavor to secure digital environments.
Conclusion
In summary, strong password encryption methods play an indispensable role in the realm of cybersecurity. Their ability to transform accessible information into secured data formats guards against unauthorized access and data breaches. The diverse array of encryption algorithms available offers numerous options for organizations to tailor their security measures to specific needs. Through the deployment of these sophisticated technologies, the integrity and confidentiality of sensitive information are assured. It is evident that a strategic approach to implementing and updating encryption methods is paramount for sustaining strong security defenses. In a world where digital threats are constantly evolving, maintaining robust encryption strategies ensures resilience and trust in the security processes of any organization.