In the digital age, safeguarding personal and sensitive information from unauthorized access is paramount. The foundation of digital security begins with the creation of strong passwords—an essential aspect of protecting one’s online presence. The importance of a secure password cannot be overstated, as it serves as the first line of defense against cyber threats. Crafting a password that is both strong and memorable requires adherence to specific guidelines designed to maximize security while ensuring user-friendliness. This article delves into the best practices for creating robust passwords, offering insights and recommendations grounded in formal guidelines for strengthening digital security.
Read Now : Effective Affiliate Content Strategies
Principles of Crafting Robust Passwords
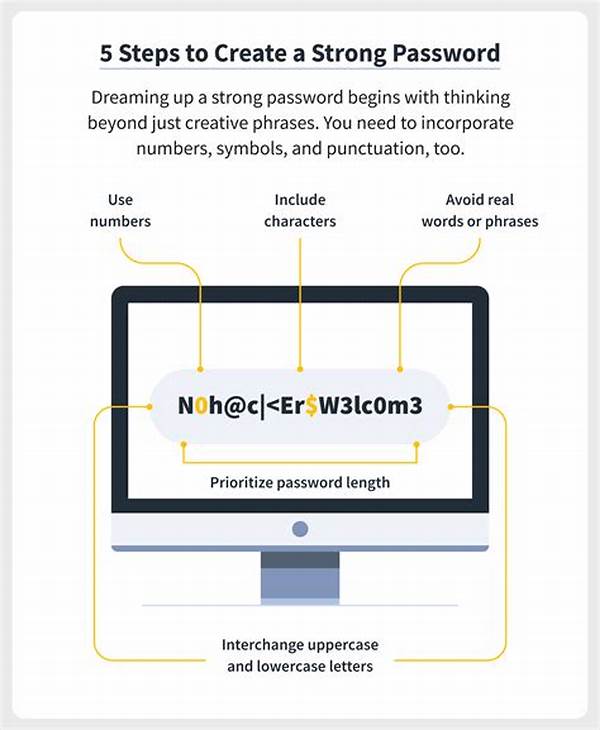
To ensure maximum security, it is critical to follow strong password creation guidelines. A robust password is characterized by its complexity and unpredictability. It should be a minimum of twelve characters, comprising a mix of uppercase and lowercase letters, numbers, and special symbols. Avoid using easily guessable passwords such as “password123” or personal information like birthdays. Instead, focus on random combinations that make it difficult for attackers to crack. Additionally, each account should possess a unique password to prevent a single compromised password from leading to broader unauthorized access. Implementing these strong password creation guidelines not only enhances security but also fosters a secure user environment. Regularly updating passwords further fortifies digital defenses, ensuring that any potential vulnerabilities are promptly addressed. Users are encouraged to adopt password management tools to store complex passwords securely, simplifying the process of maintaining multiple distinct passwords.
Strategies for Effective Password Management
Adopting strong password creation guidelines is essential in establishing a secure digital footprint. One method involves utilizing passphrases—an assemblage of random words that form a sentence or phrase. This approach enhances memorability while maintaining complexity. Another strategy includes the integration of two-factor authentication, adding an additional layer of security by requiring a second form of verification beyond the password. The utilization of password managers is also highly recommended for those managing numerous accounts, as they offer secure storage and automatic generation of strong passwords. It is imperative to avoid using the same password across different platforms to mitigate the risk of widespread breaches. Furthermore, users should remain vigilant by periodically reviewing and updating their passwords, ensuring adherence to current security guidelines. Embedding cybersecurity awareness within organizational practices is crucial, promoting a culture of vigilance and proactive security measures. Finally, education on common phishing tactics and cyber threats can empower users to recognize and avoid potential security breaches.
Importance of Strong Password Creation Guidelines
Implementing strong password creation guidelines is integral to secure personal and professional information. Passwords serve as the primary barrier against unauthorized access, making their strength and uniqueness vital. In today’s digital landscape, where cyber threats are increasingly sophisticated, ensuring your passwords adhere to recommended guidelines can significantly diminish the likelihood of a security compromise. It is crucial to educate oneself and others on the habitual practice of crafting strong passwords as part of a broader online security strategy. By investing time and resources into understanding and applying these guidelines, individuals and organizations can better safeguard their digital assets against potential threats.
Key Components of Strong Password Creation
Understanding Strong Password Creation Guidelines
1. Length: A password should be at least twelve characters long. The longer the password, the more secure it tends to be.
2. Complexity: Include a variety of characters, such as uppercase and lowercase letters, numbers, and symbols.
3. Uniqueness: Each password should be unique to each account, reducing vulnerability to multi-account breaches.
4. Randomness: Avoid obvious patterns or common words; randomness enhances security.
5. Avoid Personal Information: Do not use easily obtainable personal details such as names, birthdates, or addresses.
6. Secure Storage: Use a password manager to securely store complex passwords.
7. Regular Updates: Change passwords regularly to mitigate potential security risks.
Read Now : Startup Leadership Development Tools
8. Two-Factor Authentication: Supplement passwords with a second security measure for increased protection.
9. Passphrases: Use memorable yet complex passphrases as an alternative to traditional passwords.
10. Knowledge of Threats: Stay informed on current cybersecurity threats and strategies.
11. Avoid Reuse: Never reuse passwords across different sites to enhance security.
12. Educate Others: Share the importance of following strong password creation guidelines with peers and colleagues.
Rationale Behind Strong Password Creation
The rationale for adhering to strong password creation guidelines lies in the necessity to protect sensitive data from unauthorized entities. Strong passwords are not merely an additional precaution; they are central to any effective cybersecurity protocol. Cybercriminals employ sophisticated tactics, including brute-force attacks and phishing scams, in an attempt to gain unauthorized access to private information. By establishing a strong standard for password creation, users can bolster their defense against such threats. Organizations must enforce these guidelines across all levels to ensure a unified and robust security framework. Moreover, a culture of continuous education and awareness about evolving cybersecurity practices encourages proactive adaptation to new threats. Understanding these dynamics is integral to fostering a secure digital environment and minimizing potential breaches. Therefore, strong password creation is not only a recommendation but an essential component of an effective cybersecurity strategy.
Conclusion on Strong Password Creation Guidelines
To conclude, the implementation of strong password creation guidelines is imperative in fortifying one’s digital defenses. By embracing best practices such as complexity, uniqueness, and the avoidance of personal information, individuals can significantly enhance their online security posture. Supplementary tools like password managers and two-factor authentication further augment these defenses, providing a comprehensive approach to securing digital identities. Regular updates and a proactive stance in adapting to evolving cyber threats ensure that security measures remain effective over time. It is therefore incumbent upon both individuals and organizations to prioritize the establishment and maintenance of robust password practices as a fundamental element of their cybersecurity strategies. Through consistent education and adherence to strong password creation guidelines, the battle against unauthorized access can be effectively waged, safeguarding valuable information and securing a digital future.
Summary of Strong Password Creation Guidelines
In summary, strong password creation guidelines are essential in establishing a robust defense against cyber threats. By ensuring passwords possess length, complexity, and uniqueness, individuals can significantly reduce the potential for unauthorized access. The use of password managers and additional security measures like two-factor authentication further enhances these defenses. Regularly updating passwords and avoiding the reuse of passwords across multiple platforms is also crucial in maintaining security. Organizations can instill these practices by promoting awareness and education on cybersecurity risks and strategies. Ultimately, adherence to strong password creation guidelines is a proactive step in ensuring personal and organizational digital safety. By fostering a culture of vigilance and adaptability, the integrity of digital information can be preserved in an increasingly complex and interconnected digital world.