Importance of Integrating Cybersecurity Risk Practices
In today’s interconnected digital landscape, the imperative to protect organizational assets from cyber threats cannot be overstated. Integrating cybersecurity risk practices is paramount for safeguarding critical data, ensuring privacy compliance, and maintaining the organization’s reputation. Effective integration requires an awareness of potential vulnerabilities and a proactive approach to managing them. By embedding cybersecurity strategies within the organizational framework, companies can better anticipate and mitigate risks, thereby reducing the likelihood of a security breach. Furthermore, this approach empowers employees at every level to recognize and respond to potential threats effectively, contributing to a holistic defense mechanism.
Read Now : Innovation Hubs And Startup Accelerators
Organizations must cultivate a culture where cybersecurity is not an afterthought but a core component of their strategic planning. Integrating cybersecurity risk practices involves the continuous evaluation of existing security protocols and the timely updating of policies to counteract emerging threats. Providing training and resources to stakeholders ensures that cybersecurity awareness is prevalent at every tier of the organization. This comprehensive strategy not only enhances cybersecurity posture but also aligns with regulatory requirements and stakeholder expectations, thereby fostering trust and long-term sustainability.
Furthermore, integrating cybersecurity risk practices involves leveraging advanced technologies such as AI and machine learning to detect and neutralize threats in real-time. The dynamic nature of cyber threats necessitates a proactive stance that combines both technological and human elements. By adopting a multi-layered defense strategy, organizations can better withstand sophisticated attacks while maintaining business continuity. Thus, a proactive engagement in cybersecurity ensures resilience, enabling the organization to thrive in the digital era.
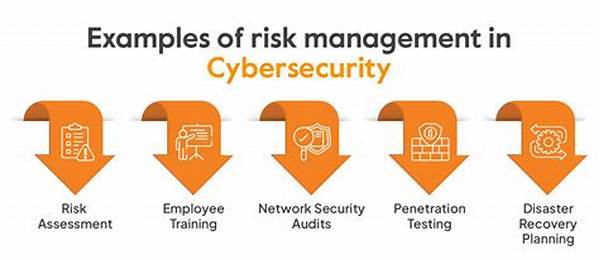
Steps in Integrating Cybersecurity Risk Practices
The integration of cybersecurity risk practices begins with a comprehensive risk assessment. This involves identifying critical assets and potential threats that may affect them. By understanding the organization’s risk exposure, strategies can be formulated to protect these assets effectively.
Developing a robust cybersecurity framework is essential in integrating cybersecurity risk practices. This involves establishing guidelines, policies, and procedures that govern how cybersecurity is managed within the organization. A well-defined framework facilitates consistency and standardizes practices across all departments.
Educating employees on the importance of cybersecurity is crucial. Integrating cybersecurity risk practices includes training programs that enhance employees’ ability to recognize potential threats and respond appropriately. This reduces the likelihood of human error, which is often a significant factor in security breaches.
The utilization of advanced technologies forms a vital component in integrating cybersecurity risk practices. By leveraging tools like AI and machine learning, organizations can anticipate and respond to threats more effectively. This technological support complements human efforts and enhances the overall cybersecurity stance.
Continuous monitoring and evaluation are imperative for effective integration. Identifying and rectifying vulnerabilities is an ongoing process that requires diligence and adaptability. Through regular assessments, organizations can fine-tune their strategies, ensuring sustained protection against evolving threats.
Monitoring and Evaluating Cybersecurity Risk Practices
Continuous monitoring and evaluation are essential aspects of integrating cybersecurity risk practices within an organization. It involves a systematic approach to review and analyze the efficacy of current security measures. By consistently evaluating practices, organizations can promptly identify vulnerabilities and adapt their strategies to address emerging threats. This ongoing scrutiny ensures that security measures remain robust and effective in an ever-changing digital landscape.
Additionally, effective monitoring involves the deployment of automated systems and tools that facilitate real-time surveillance and analysis. Integrating these technological solutions with traditional security protocols provides a comprehensive defense strategy. Furthermore, periodic audits and assessments, conducted by external experts, serve as an added layer of scrutiny, ensuring that the organization’s cybersecurity efforts remain aligned with industry standards and regulations. Through diligent monitoring and evaluation, organizations can foster a culture of continuous improvement and resilience, which is vital in mitigating cybersecurity risks.
Key Factors in Effective Integration of Cybersecurity Practices
1. Executive Support: Strong leadership is crucial in driving the integration of cybersecurity risk practices. Executive buy-in ensures adequate resources and attention are allocated towards cybersecurity initiatives.
2. Comprehensive Strategy: A holistic approach that incorporates technical, administrative, and physical safeguards is essential. This comprehensive strategy enhances the organization’s ability to withstand various cyber threats.
3. Risk Assessment: Regular risk assessments help in identifying potential vulnerabilities and forecasting future challenges, enabling proactive mitigation strategies in integrating cybersecurity risk practices.
4. Employee Awareness: Continuous training programs enhance awareness and competency among employees, reducing the likelihood of human error compromising security measures within the organization.
5. Technical Infrastructure: Robust technical infrastructure provides a strong foundation for security initiatives, integrating cybersecurity risk practices effectively to safeguard digital assets.
6. Policy Development: Establishing clear policies and procedures ensures standardization in security practices, facilitating seamless integration and compliance across the organization.
Read Now : Coordination Skills For Ballet Dancers
7. Incident Response Plan: A well-defined incident response plan ensures rapid and effective reaction to security breaches, minimizing potential damage.
8. Vendor Management: Establishing security requirements for third-party vendors prevents external vulnerabilities from impacting the organization’s security posture.
9. Regulatory Compliance: Adherence to regulatory standards ensures that the organization meets legal requirements and protects itself from potential compliance-related penalties.
10. Threat Intelligence: Utilizing threat intelligence informs preventive measures and enhances situational awareness, thus bolstering security efforts.
11. Regular Audits: Periodic audits provide an external perspective on the organization’s cybersecurity posture, identifying areas for improvement and reinforcing existing practices.
12. Innovation Adaptability: Keeping abreast with technological advancements ensures the organization can adapt to new cybersecurity innovations, maintaining a competitive edge in threat management.
Challenges in Integrating Cybersecurity Risk Practices
The integration of cybersecurity risk practices is fraught with challenges that organizations must navigate to establish robust security frameworks. One primary obstacle is the constantly evolving nature of cyber threats, which demands that organizations consistently update their security measures. Additionally, there is often a significant gap between available cybersecurity solutions and their implementation due to resource constraints or a lack of technical expertise. Such challenges necessitate strategic planning and investment to overcome, ensuring that security measures remain comprehensive and effective.
Another challenge in the integration process pertains to internal resistance within organizations. Employees may resist changes to established workflows or underestimate the importance of cybersecurity measures. Overcoming this requires a cultural shift wherein cybersecurity becomes a shared responsibility across the organization. By fostering understanding and engagement through continuous training and communication, organizations can effectively mitigate internal resistance, thereby facilitating the seamless integration of cybersecurity risk practices.
Future Outlook of Integrating Cybersecurity Risk Practices
The future of integrating cybersecurity risk practices is poised for significant evolution, driven by technological advancements and increased regulatory scrutiny. As organizations embrace digital transformation, the scope and complexity of cybersecurity challenges will expand, necessitating refined strategies and solutions. The integration of AI, machine learning, and other cutting-edge technologies will become mainstream, offering enhanced threat detection and response capabilities. This technological evolution will demand that organizations remain agile, adapting to new tools and methodologies to maintain robust security frameworks.
Moreover, regulatory bodies are actively enhancing cybersecurity guidelines, compelling organizations to comply with more stringent requirements. Integrating cybersecurity risk practices will, therefore, involve aligning with evolving regulations to avoid potential penalties. Organizations must invest in continuous learning and improvement processes to remain compliant. By embracing innovation and regulatory alignment, the integration of cybersecurity risk practices will evolve to address sophisticated threats, ensuring the protection of vital assets and promoting resilience in a dynamic digital ecosystem.
Summary: Integrating Cybersecurity Risk Practices
In summary, integrating cybersecurity risk practices is an indispensable component of modern organizational strategy. It involves an intersectional approach, combining technology, human resources, and policy development, to effectively safeguard against pervasive cyber threats. At its core, this integration aligns digital security measures with organizational objectives, cultivating a protective environment that is proactive rather than reactive. Organizations adopting this paradigm are better equipped to navigate the complexities of the digital landscape, ensuring continuity and stability in their operations.
The process is continuous, with regular assessments and updates needed to accommodate ever-evolving threats. By embedding cybersecurity risk practices into organizational culture, companies not only fortify their defenses but also instill a sense of collective responsibility among employees. This approach ensures that security is a shared endeavor, promoting vigilance and cooperation across all levels. Ultimately, integrating cybersecurity risk practices fosters a resilient digital infrastructure, empowering organizations to thrive amid increasing cyber threats and securing a sustainable future.