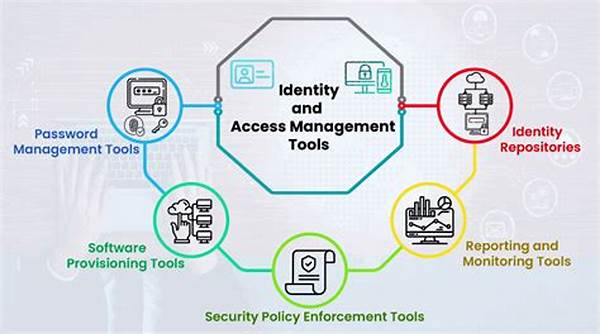
In today’s increasingly digital world, safeguarding sensitive information and ensuring secure access to systems are paramount for organizations. As such, Identity and Access Management (IAM) tools have become indispensable components in fortifying digital infrastructures. These tools are designed to manage user identities, authenticate users, authorize access, and maintain comprehensive surveillance of system interactions. Through the deployment of identity and access management tools, organizations can not only bolster their security posture but also streamline operations, enhancing both user experience and administrative efficiency. The intricate processes involved in IAM solutions require careful selection and implementation to best meet an organization’s unique needs.
Read Now : Cross-border Technological Advancements
The Importance of IAM Tools in Cybersecurity
Identity and access management tools are critical in the realm of cybersecurity. These tools help organizations manage digital identities and enforce policies pertaining to user access rights. The primary objective of IAM tools is to ensure that the right individuals have the appropriate access to technology resources. Additionally, these tools play a crucial role in audit and compliance efforts by providing detailed logs and reports on user activities. This comprehensive oversight is essential for meeting regulatory requirements and maintaining robust security protocols. Identity and access management tools are inherently designed to curb unauthorized access, effectively mitigating potential security breaches. As the technology landscape evolves, so too must the strategies implemented by organizations to protect sensitive information. Consequently, IAM tools have become central to the development of adaptive security frameworks, ensuring that organizations remain resilient in the face of emerging threats.
Key Functions of IAM Tools
1. User Provisioning and Deprovisioning: Identity and access management tools facilitate the efficient management of user accounts. This involves the creation, modification, and removal of user permissions, ensuring individuals have the right access at all times.
2. Single Sign-On (SSO): With identity and access management tools, users can enjoy streamlined access to multiple applications using a single set of credentials. This feature enhances user experience while maintaining strong security measures.
3. Multi-Factor Authentication (MFA): IAM tools ensure increased security by requiring multiple forms of verification before granting access, reducing the risk of unauthorized access.
4. Access Governance: These tools provide powerful analytics and reporting capabilities that help organizations monitor and control user access across different platforms and systems.
5. Compliance Management: Identity and access management tools offer comprehensive audit trails and reporting functions that aid organizations in meeting regulatory compliance requirements.
Read Now : Advanced Classical Ballet Lesson Plans
Choosing the Right IAM Tools
In selecting the most suitable identity and access management tools, organizations must conduct thorough evaluations based on their specific requirements and operational landscape. The starting point involves understanding the organization’s current IT environment and identifying potential security vulnerabilities. It’s crucial to engage stakeholders from various departments to gather a comprehensive understanding of organizational needs. Further, an assessment should be made regarding the integration capabilities of IAM tools with existing systems and technologies. This ensures seamless operations and minimizes disruptions. Additionally, scalability must also be considered to accommodate future growth and evolving security demands. Organizations should opt for IAM solutions that offer robust support services, ensuring that any operational challenges can be swiftly addressed. Lastly, cost analysis is essential to guarantee that the selected identity and access management tools provide a substantial return on investment.
Implementing IAM Tools
Implementing identity and access management tools involves several crucial steps to ensure operational success and security enhancement. It begins with strategic planning, which encompasses defining clear objectives and expected outcomes. This process involves collaboration across technical teams and key stakeholders to align goals. Once the strategy is established, a phased implementation approach is advisable, allowing for continuous assessment and adjustments. Testing plays an integral role, ensuring the tools function seamlessly and securely integrate with existing systems. Data migration and integration processes are handled meticulously to avoid data loss or security lapses. Training and change management are vital components, equipping users with the knowledge to effectively utilize IAM tools and embrace new security protocols. Regular monitoring and evaluation ensure sustained performance and uncover areas for optimization.
Emerging Trends in IAM Tools
The realm of identity and access management tools is witnessing dynamic evolution, driven by technological advancements and emerging cybersecurity threats. Artificial intelligence (AI) and machine learning are increasingly integrated into IAM solutions, enabling automated anomaly detection and predictive analytics for enhanced security. The adoption of cloud-based IAM systems is rapidly growing, providing scalability and flexibility to organizations. Additionally, there is a heightened focus on zero-trust security models, requiring validation at every access point. Moreover, biometric authentication methods, such as facial recognition and fingerprint scanning, are gaining traction within IAM tools, offering enhanced security measures. These trends reflect a shift toward more adaptive and intelligent IAM solutions, capable of addressing the complex demands of modern digital environments. Organizations must stay abreast of these innovations to effectively safeguard their assets and remain competitive in the evolving digital landscape.
Conclusion
Identity and access management tools are indispensable for modern organizations seeking to protect their digital assets and ensure secure user interactions. By implementing these tools, organizations can effectively manage user identities, enforce access policies, and maintain comprehensive security oversight. The evolving landscape of IAM tools, driven by technological advancements and emerging trends, necessitates adaptive strategies and continuous evaluation to address the intricate security needs of today’s digital environment. Ultimately, the careful selection, implementation, and management of identity and access management tools serve as a cornerstone for robust cybersecurity frameworks, underpinning organizational resilience and information protection endeavors across diverse industries.